Today we are going to learn DOS and DDOS attack techniques. Denial-of-service (DOS) is an attack crashes a server, or make it extremely slow. DOS is typically accomplished by flooding the targeted machine or resource with superfluous requests in an attempt to overload systems and prevent some or all legitimate requests from being fulfilled. In simple words by DOS attack an attacker sends a lots of useless traffic to targeted website or server or network that because the system can't handle this very huge amount of requests, and the system goes down, no one can use the system. As we all know that every server have traffic limits if the requests are more then the traffic limit at once the server becomes very slow or even it can crash. This technique is called DOS (Denial-Of-Service) attack.
DDOS is Distributed Denial-of-Service attack. DOS is the attack which performed from one computer to one targeted network, in DOS a single machine sends millions of useless traffic on a network but in the case of DDOS many attacker machine targets one network and every attacker machine is performing DOS. That means each and every attacker machine sends millions of traffics. DOS becomes useless against high capacity servers because larger servers easily manages millions of traffics. In such cases the attacker needs thousands or more machines from various networks to knee down the target, this is DDOS attack. To do this DDOS attacker need a organized group of hackers or botnets. Hacking group Anonymous is famous for their DDOS attacks.
Black hat hackers uses DDOS to slow down or crashes high profile web servers like banks or payment gateways, for revenges or blackmail and activism.
DOS attack can perform easily using various tools like
There are also various types of DOS attack techniques:DDOS is Distributed Denial-of-Service attack. DOS is the attack which performed from one computer to one targeted network, in DOS a single machine sends millions of useless traffic on a network but in the case of DDOS many attacker machine targets one network and every attacker machine is performing DOS. That means each and every attacker machine sends millions of traffics. DOS becomes useless against high capacity servers because larger servers easily manages millions of traffics. In such cases the attacker needs thousands or more machines from various networks to knee down the target, this is DDOS attack. To do this DDOS attacker need a organized group of hackers or botnets. Hacking group Anonymous is famous for their DDOS attacks.
Black hat hackers uses DDOS to slow down or crashes high profile web servers like banks or payment gateways, for revenges or blackmail and activism.
DOS attack can perform easily using various tools like
- Nemesy
- RUDY
- GolodenEye
- UDP flood
- PyLoris
- HULK
- ToR's Hammer
- xerxess
- LOIC
- HOIC
- MetaSploit
- Distributed volume based DOS attack
- Degradation of service attacks
- Application-layer floods
- DDOS extortion
- HTTP POST DOS Attack
- Internet control message protocol (ICPM) flood
- R U Dead-Yet (RUDY)
- Nuke
- Peer-to Peer attacks
- Permanent denial-of-service attacks
- Reflected/spoofed attack
- shrew attack
- (S)SYN Attack
- Teardeop attacks
- Telephony denial-of-service (TDOS)
The screenshot of the command is following:
Then we type cd command to navigate in to Slowloris's directory:
Then we need to run Slowloris Python script. Here we need the IP address of the targeted server or website in our case it is 127.0.0.1 that is our localhost. The command of DOS attack using Slowloris will be as following:
This attack is slow down our loaclhost server.
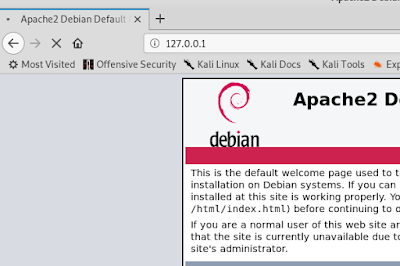 |
| Look it is loading ..... |
 |
| Here we need to wait for server's response |
This article is only for educational or informational purpose only. The author is not responsible for any illegal activity. KaliLinux.In does not promote any malicious activities.


