Hey Folks, as we know that whenever we need to do a phishing attack, we use github tools and to execution them we need an operating system such as : kali linux, parrot os etc. But sometimes due to various reasons we are not able to reach the localhost machine, that’s why we use many types of paid cloud services. But through this tutorial we will show how we can perform phishing attacks from anywhere using free Google cloud services.
Lets take a look 🙂 !!
Before starting the tutorial, let us tell you that you can use this technique through your android phone after which you will not need to download external application. Let us first give you a short introduction about the google cloud shell. “Cloud Shell provides you with command-line access to your cloud resources directly from your browser“. Now first go to the website and login through any Google account from here. That’s it, your kali linux operating system is ready to access from anywhere.
You do not need any guidelines to control this cloud service as it will be easily controlled by beginners. Back to the work 🙂 !! We assume that you have created your account on google cloud shell, Now take a phishing tool from GitHub and try to install and configure it. In our case we will choose our favorite phishing tool called “Advphishing“. Copy the below command and execute on the cloud terminal.
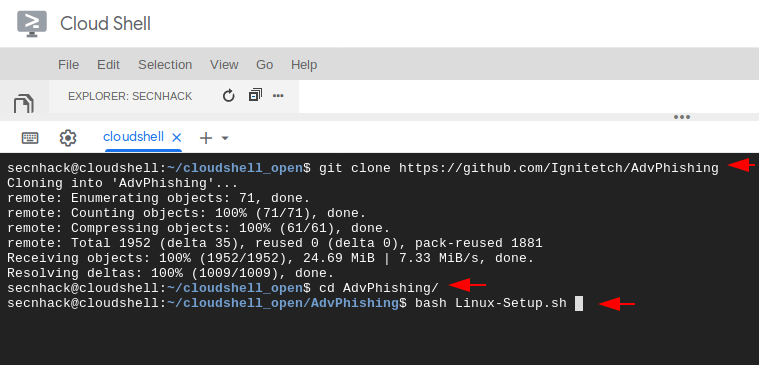
Note : If you are using the kali linux then we have to use the same command to install this tool.
Sounds good 🙂 !! Our idea has worked and below you have to give your ngrok token that you can opt from here.
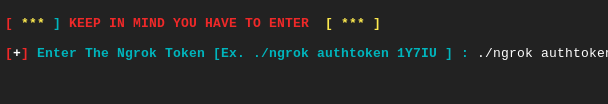
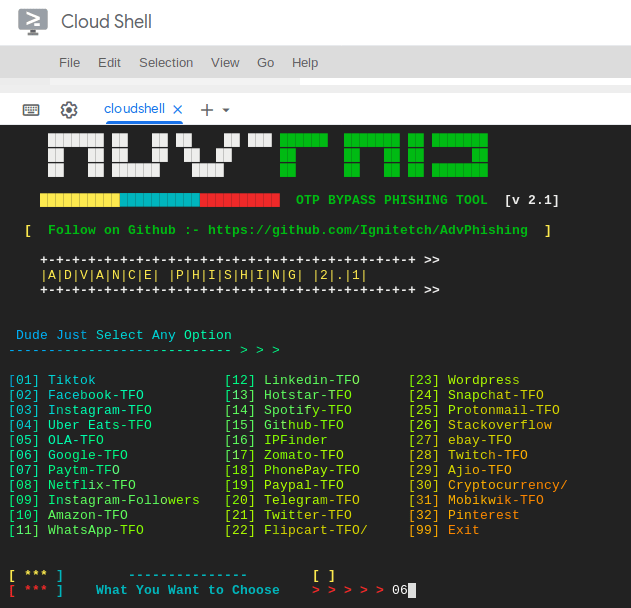
Great 🙂 !! As you saw above that the tool is successfully installed and configured on the terminal without any errors and even to set it up we didn’t have to install any external dependencies. Now choose any option you want to create a phishing page.
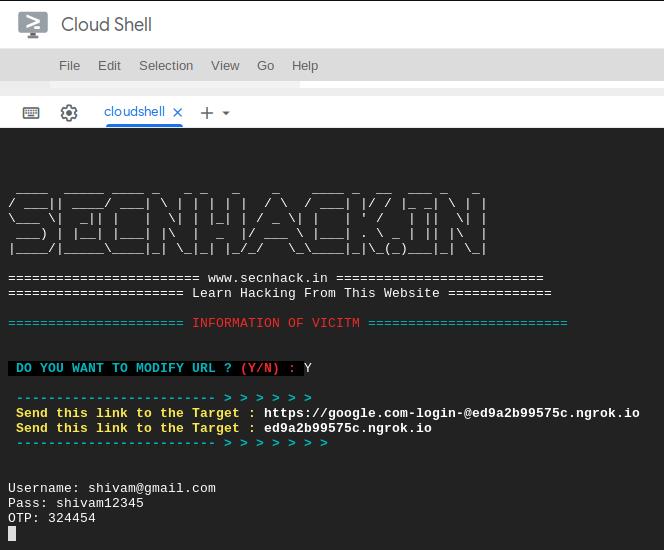
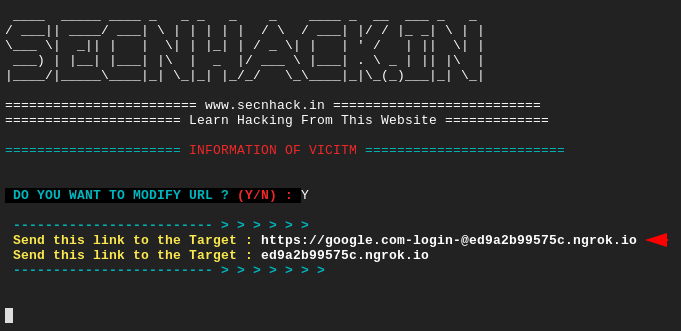
The tool modifies the phishing link first and gives us a real domain phishing link so that anyone can easily cheat.
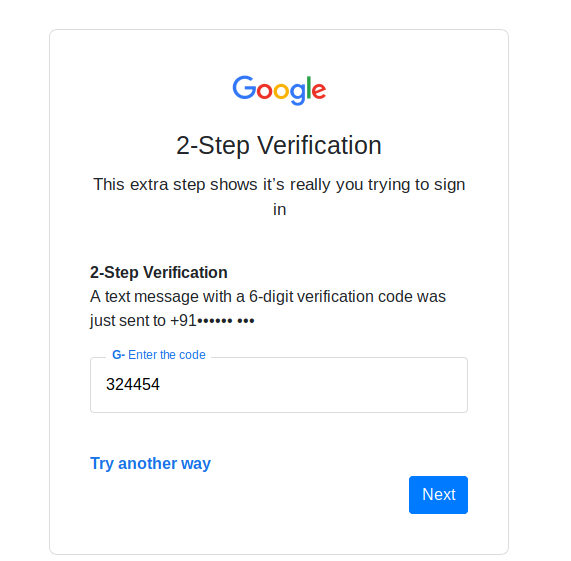
Nice 🙂 !! In this tool has two factor authentication phishing page, so If anyone gets stuck on the OTP then through this tool they can bypass it by entering OTP from the victim.
Alright 🙂 !! The final results will come here and you can see that we have successfully obtained the credentials of the victim through Google Cloud Shell. Similarly you can use the tools and access your account from anywhere.